A sample text widget
Etiam pulvinar consectetur dolor sed malesuada. Ut convallis
euismod dolor nec pretium. Nunc ut tristique massa.
Nam sodales mi vitae dolor ullamcorper et vulputate enim accumsan.
Morbi orci magna, tincidunt vitae molestie nec, molestie at mi. Nulla nulla lorem,
suscipit in posuere in, interdum non magna.
|
Well, it took a little bit of time, but the Administrative Office of the U.S. Courts has issued revised jury instructions, recommended for all federal cases, updated for today’s social media age. It’s “old wine in new bottles” — i.e., traditional rules adapted to new social networking communications — which illustrates that some things really should not (and do not) change at all where social media are concerned.
Federal Court Officials Issue Guidance on Jury Use of Blackberries, iPhones, Twitter, LinkedIn Etc. [TechLaw].
You may not communicate with anyone about the case on your cell phone, through e-mail, Blackberry, iPhone, text messaging, or on Twitter, through any blog or website, through any internet chat room, or by way of any other social networking websites, including Facebook, My Space, LinkedIn, and YouTube.

http://shortyawards.com/glennm
Hey, it’s hardly an Oscar or People’s Choice award, but this rocks!!
Posted via email from glenn’s posterous
In my view, the second sentence here is the most important. If one posts material viewable by the entire world, the author implicitly licenses anyone to use the content-—in other words, no copyright applies, and the author does not “own” his or her user-generated content. The necessary corollary is that when the whole world can see your stuff, the government does not need permission, let alone a warrant, to look too.
Privacy law was largely created in the pre-Internet age, and new rules are needed to keep up with the ways people communicate today. Much of what occurs online, like blog posting, is intended to be an open declaration to the world, and law enforcement is within its rights to read and act on what is written. Other kinds of communication, particularly in a closed network, may come with an expectation of privacy. If government agents are joining social networks under false pretenses to spy without a court order, for example, that might be crossing a line.
Of course, where a social network allows users to restrict access, to friends or followers, the opposite conclusion holds. For instance, unless Facebook wall posts are made available to “everyone” in the user’s privacy settings, then there remain both legitimate ownership and privacy interests, such that the government can’t monitor that content without both probable cause and a warrant.
[Part I of this series of essays can be found at this permalink, Part II at this permalink].
3. Trademarks, Genericide & “Twittersquatting”
Let’s assume, for purposes of discussion, that social media content — not limited to Tweets — cannot be trademarked. Whether that is correct will be ultimately determined, at some point, by a combination of the PTO and the U.S. Court of Appeals for the Federal Circuit. What that (reasonable) assumption indicates is that trademark law is far more important for existing trademark holders who either (a) venture into the social stream and real-time Web in order to market and promote their brands, or (b) are confronted with third-parties using their trademarks, whether for commentary or profit, without consent, than it is for social media users generally.
(a) The Aspirin of Social Media. Trademarks are property rights, both under US common law and pursuant to federal statute, the validity of which often hinges on two discrete issues — first use and “genericness.” People tend to forget that Bayer AG first invented aspirin in 1897 but lost its rights to the brand name in the United States by allowing it to escape into the public domain, i.e., go generic or commit “genericide,” a tragic commercial fate shared famously by Duncan Yo-Yo Co. (yo-yo) and Otis Elevator Corp. (escalator), among others. Generic terms of course cannot be trademarked. As a result, such companies and products as varied as Xerox (photocopying), Kleenex (facial tissue) and Johnson & Johnson (band-aid) have stepped up outreach and litigation efforts to curtail use of the trademarked brands as nouns and to constrain their own usage, for instance by changing advertising jingles to add “brand” to the name (going from “I’m stuck on Band-Aids, ’cause Band-Aid’s stuck on me” to “I’m stuck on Band-Aid brand, ’cause Band-Aid’s stuck on me.”)
Welcome to Web 2.0, corporate IP police! Your task in protecting against genericide has become an order of magnitude harder because social media is immediate, difficult to search and presents such massive volume of content that periodic review of even a portion of it is clearly impossible. But as the historic lessons show, doing nothing risks colloquial usage of marks in ways that conflict with trademark holders’ long-term interests. There is no substitute for perseverance, hard as it may be in the context of real-time social streams.
Perhaps most vexing is that these very risks can be presented by a company’s best customers, its “fans.” As PR specialist Rob Clark of the SMG Group notes:
So we all know the story. Imagine, a group of faithful enthusiasts falls in love with Super-Duper Brand (for the purposes of this illustration I’m using a fictitious name). They start a forum at superduperrocks.com, the maintenance of which they cover by selling superduperrocks t-shirts and other merchandise. A lawyer for Super Duper stumbles upon the site and fires off a standard cease and desist letter to attend to the trademark infringement. The community freaks out, both in terror of what a visit to court may cost and in anger of being turned on by the brand they adored and revered. The pundits point a spotlight on the issue and chuckle over what a stumble, what a gaffe, “who could possibly be foolish enough to attack your greatest evangelists?” Those who rail against the new media tools will waggle their fingers and declare, “These interwebs will doom us all.”
That’s a debacle in the making. The IP lawyer was obviously correct, but crowd-sourced demand letters will likely do more to alienate fans than protect the mark. The balance between heavy-handed legal cease-and-desist letters, litigation and consensual licensing of permissible uses represents a major challenge to trademark holders in the emerging era of social media.
(b) Safe Harbors, Impersonation and Infringement. So if that’s not bad enough, take the question of how trademark holders can prevent others from infringing (or diluting) their marks by scarfing up the words as profile identifiers on social media sites. The short answer is, like all mark protection activities, vigilance. Yet as addressed in this section, at present the law is still developing and the statutory rules established to deal with improper use of protected trademarks on the Internet — mainly in the domain name and copyrighted content (music, movies, etc.) contexts — do not squarely apply to social media and the real-time Web.
It would be a pleasure, for my ISP and Web site clients, to report that the statutory safe harbor granted to Internet access providers — commonly known as “notice-and-takedown” — protects them against litigation for trademark infringement by social media users. But that’s not necessarily the case at all.
First, the immunity provided to interactive computer services under the Communications Decency Act (47 U.S.C. § 230) applies only to screening and blocking of child pornography and other offensive Internet content, while the DMCA safe harbor in 17 U.S.C. § 512 is inapplicable if a “service provider” receives any “financial benefit directly attributable to the infringing activity” and “has the right and ability to control such activity.” Whether the courts will construe these terms expansively is unclear. Yet it is clear that at least some social media providers both receive financial gain (which may not mean profitability, by the way), including advertising revenues, and have the ability to arrest infringing conduct by users. So while removing allegedly infringing UGC or profiles is a good business practice, it does not mean legal liability is eliminated.
Second, the provisions of the Anti-Cybersquatting Consumer Protection Act, 15 U.S.C. § 1125(d), limit the protection accorded vis-a-vis trademark holders to entities assigning “domain names,” defined narrowly as “alphanumeric designation which is registered with or assigned by any domain name registrar, domain name registry, or other domain name registration authority as part of an electronic address on the Internet.” Social media profiles do not yet fall under this statute, at least facially.
So even in the case of simple “Twitterquatting” — the allocation by a social media network provider of a user name to someone who is either not the real person or who is using a trademarked phrase without permission — there is no compelling case to be made today for statutory immunity. Recall that, in the early days of the commercial Web, Network Solutions (now VeriSign) was sued frequently by trademark holders under contributory infringement, conversion, negligence, unfair competition and other traditional causes of action for registering trademarks as domain names to people without legal rights to the marks. See, e.g., Lockheed Martin Corp. v. Network Solutions, Inc., 193 F.39 980 (9th Cir. 1997). And more recently, Google has litigated a series of cases in which famous brands (Vuitton, etc.) have alleged, with mixed results, that its AdWords program represents use by Google, as opposed to the advertisers paying for such keywords, of a protected mark in commerce, thus exposing Google to potential damages liability. (I personally don’t agree with this legal theory, but the fact is that it has been accepted by a minority of courts.)
All of these theories, which parallel the claims brought by AOL and other ISPs against spammers before Congress made unsolicited commercial email illegal with the CAN-SPAM Act of 2003, can be asserted unless and until legislation is passed creating a national standard and preempting state law. For instance, in his well-publicized (but later withdrawn) lawsuit against Twitter, Tony La Russa claimed that use of his name by another Twitter member constituted Lanham Act violations (trademark infringement, false designation of origin, dilution of a famous trademark), invasion of privacy under California Civil Code § 3344 and misappropriation of name and likeness.
It is no wonder, then, both Twitter and Facebook have established means by which rights holders can protect their trademarks from unauthorized use. For Facebook, these include:
- Filing their trademark(s) online with Facebook, which will prevent any third-party users from acquiring the filed trademark as a username. (Filing requires the name of the company, the trademark to protect, the federal registration number of the mark and the filer’s title and email address.)
- Not authorizing transfer or sale of user names in the hope that this will eliminate squatting or profit-driven transfers.
- Maintaining an online IP Infringement form which allows rights holders to protest after-the-fact unauthorized uses of their intellectual property.
Not unusually (see Part II), Twitter does things a little differently. The Twitter terms of service (ToS) grant it the right to remove or suspend unilaterally any account that appears to or is claimed to violate another’s trademark rights. These notice-and-takedown provisions are based on a “clear intent to mislead people” as the test for suspending unauthorized accounts. However, they explicitly allows parody impersonation, using a standard of whether a “a reasonable person be aware that it’s a joke” as the criterion for a parody. (The fact that the La Russa impersonator prominently labeled his profile as a fake plainly did noting to deter litigation, of course.) And those same guidelines have not stopped corporations from suing Twitter when they suspect others are “diluting” their marks, even before response to a takedown demand. Twitter has also responded as a business matter with a so-called “verified account” program for public figures.
Now on the substance of parody or so-called “gripe” users, trademark law is gradually becoming clearer, and works to favor the social media site rather than the personality. There are numerous obstacles with use of federal trademark law to prosecute a gripe user. Trademark infringement claims require that the defendant use the plaintiff’s mark, without consent,”in commerce” — a term that generally refers to the sale of a product. Parodies and product criticisms may use a plaintiff’s name or mark,but typically not to sell anything, rather to complain about or poke fun at the company. Trademark claims also demand that the defendant’s unapproved use of the mark must have confused reasonable consumers. However, because such third-party sites and content typically attack or lampoon the trademark holder, there is little risk that consumers could ever reasonably believe that such a site was operated by the trademark owner.
A recent Sept. 2009 decision by U.S. District Judge T.S. Ellis in Virginia, Bernard J. Carl v. BernardJCarl.com, focused on another element of trademark law — whether an individual’s name is a protectable trademark. The general rule is that names (first or last) only qualify as trademarks if they have acquired a distinctive “secondary meaning.”
Controlling circuit authority clearly classifies the use offirst names or surnames as descriptive marks, which are inherently non-distinctive and accordingly are not protected under the Lanham Act absent a showing of distinctiveness. Thus,descriptive marks may gain the protection ofthe Lanham Act if they become distinctive by acquiring a secondary meaning within the relevant purchasing community — that is, a substantial number ofpresent and prospective consumers.
So, for instance, “Martha Stewart” probably has acquired a secondary meaning, to refer to her home decoration, gardening and food business. The same problem would arise for claims of cybersquatting, because, according to Judge Ellis, to garner protection under the ACPA a personal name must have acquired secondary meaning at the time of its registration. The implications for social media sites are obvious, namely that even if there is a legal basis to challenge so-called “Twittersquatting” for celebrity impersonation, it probably does not lie in the realm of trademark infringement.
(c) Trademarks and Deep Pockets. From the legal to the practical. All of the above is without regard to the fact that, like NSI in the 1990s, those who believe their interests or business have been damaged by use of a name, mark or other content by a social media subscriber are — as an economic imperative — inclined and very well incentivized to name as the principal defendant the company running the social network. When Hasbro had a problem with a Facebook application developer’s take off on “Scrabble” for a wildly popular Facebook game dubbed “Scrabulous,” it acted against Facebook under the DMCA, not (at least initially) against the smaller, and less well-endowed financially, developer. Likewise, when one game coder believed another had stepped on his trademark, he sued Facebook for infringement.
What these and many other anecdotes indicate is that when setting up and operating any social media site, a Web developer must take into account that it is the most visible, and some might say vulnerable, party to use of the litigation process for what I called “legalized blackmail.” (Note, I have not trademarked that phrase, so you are free to use it!) Litigation defense is a cost of doing business in modern America. And since the issue of knowledge is key to trademark defense — under the reasoning in Tiffany v. eBay Inc., social networks could be held liable for username squatting or infringement (on a contributory infringement theory), if they continue to provide services to users they know or have reason to know are engaging in infringement — programs that terminate user membership privileges at the slightest hint of unlawful use of content or marks are the best insurance.
Given the uncertainties surrounding the nascent law of social media, which as noted in Part I will most likely evolve out of the cauldron of litigation, the burden of litigation as a cost of doing business may be a steep one indeed. So as users, expect to see a whole array of self-protection measures by social media vendors. “Verified accounts” and trademark take-down complaints are just the very early start. The days of Twitter being praised for its laid-back, touchy-feely attitude towards trademarks are over, I believe, in just a short six months. And that, readers, is the speed at which things change in our world of the real-time Web!
In Part IV of this series of essays, we address the broader context of social media law, including whether there is anything really new here, or just “old wine in new bottles.”
[Part I of this series of essays can be found at this permalink].
2. Who Owns User-Generated Content?
Who owns user-generated content (UGC) posted to social media sites? This is but one of the many vexing issues presented by the emerging law of social media, albeit one of great interest to users, corporate subscribers and social networking providers alike. After all, if possession is 9/10 of the law, then the natural, lay reaction to the question of who owns social media UGC is “the Web site, of course.”
That’s not exactly correct, however. One must differentiate among the various forms of intellectual property (IP) law potentially applicable here. Copyright, a matter exclusively of federal law, is available for original expressions (with or without registration), but is always subject to “fair use.” Trademarks and their service mark complements are available for unique names, phrases and logos associated with commercial products and services, but are limited to narrow classes of expression and ordinarily — unlike copyright — must be expressly claimed. Finally, patents are available for inventions (products, processes and methods), and give the patent holder (a/k/a patentee) the power to prevent anyone else from using the protected invention, but only arise when a patent is officially issued by the Patent & Trademark Office (PTO).
(a) Social Media and IP Law. Each of these bodies of law, and the respective rights and obligations they create, has a different impact on social media generally. For instance, Twitter owns a trademark on the company’s name, but was denied registration of a trademark on “Tweet.” And in a provocative change last February, one eliciting a firestorm of user criticism, Facebook modified its terms of service (ToS) to grant the site a perpetual license on UGC even after a subscriber terminates his/her membership and removes photos and other UGC from their page. These two recent examples illustrate not only that IP law in part depends on the eye of the beholder, but more importantly that even within the social media space, there is no present consensus on just what is protected, what is public domain and what is somewhere in between.
Let’s start with the basics, then. Copyright cannot be claimed on information, only on expressions. So the information in a database or software application cannot be copyrighted, but the organization of a database and the actual code (whether in a scripting language or machine code) for a program are considered expressions subject to copyright. One would not, for instance, violate Microsoft’s copyrights by designing a word processing program that replicated functionalities of MS Word, but copying of the underlying code would be unlawful. (Don’t take this too literally, however, because the issue of software patents, including those granted to Microsoft — one of present controversy in the US — could prevent another coder from achieving the same functionality under the patent law doctrine of “equivalents,” whether or not code was actually purloined.)
Unless, that is, the copying were protected by the so-called fair use doctrine, codified at 17 U.S.C. § 107. This exception allows use of some, but not all, of an original work by another (with or without attribution), and is the basic reason why bloggers who quote portions of other posts are acting lawfully. On the other hand, lifting the entire portion of any article, whether blogged or on a traditional media site, is typically illegal without the consent (i.e., license) of the copyright holder. Yet again, if the expression itself is already in the public domain, then courts will not uphold a copyright claim, concluding either that the author “impliedly” licensed the content, abandoned any copyright in the expression, or that the material is not copyrightable in the first instance because not original.
Putting all these basic principles together yields precisely the answer posed for social media legal questions generally in Part I of this series — “it depends.” If a blogger structures his site with a full Creative Commons license, then nothing posted is subject to copyright because he has abandoned such a claim. If a Facebook user posts photographs to his or her Facebook page, and makes them available to friends, a copyright claim likely would not lie against those friends if they used the photos without permission. But, as we shall see below, these are the easy situations in which application of IP principles is (relatively) clear.
(b) Are Tweets Copyrighted? This was the question, first posed in the blogosphere by Mark Cuban in May 2009 (“Are Tweets Copyrighted?“), addressed in part in an earlier post. To summarize, a Tweet, like any other expression, can be copyrighted if original, not public domain and not impliedly licensed. But neither Mark nor anyone else (as far as this author knows) has addressed whether a Tweet, at 140 characters, is inherently too short, i.e., too superficial, to be deemed an original expression for purposes of copyright. Compare, for instance, Pat Riley’s famous trademark in the early 1990s on “three-peat” while with the L.A. Lakers. Whether the same phrase could be copyrighted is doubtful.
The point here is that social media sites cannot create rights that otherwise do not exist in the law, but can narrow or waive rights otherwise held by users with their ToS agreements. The conclusion that because Twitter has disclaimed ownership of Tweets the tweeting user must necessarily own them is a false syllogism. In other words, the language in the Twitter ToS to the effect that “what’s yours is yours” and that ”[the Twitter account owner] profile and materials remain yours‚” is merely prcatory, as lawyers say. It doesn’t bind anyone and certainly cannot govern if the copyright claim is disputed in court.
Copyrightable contents must be original, an expression (not a fact or opinion) and not merely an idea. If the material you post through Twitter isn’t copyrightable to begin with, it will not mystically transform into protectable content merely by being Tweeted, and decidedly not because, as between Twitter and its users, Twitter has technically disclaimed ownership. Hence, as one writer cogently observed:
The long and short of it is this: if 90% of all Tweets are nothing more than recitation of facts. That means that about 90% of Tweets are not protectable. For the other 10%, we’re not done with you yet. It’s all in how those facts are stated.
Twitterlogical—The Misunderstanding of Ownership. [Note to author Brock Shinen: this is most decidedly fair use!!] Also useful in this regard is an interesting blog post by PR specialist Evan Hanlon on the conflict between social media and copyright law as applied to digital music sharing.
Well, it’s not really “how the facts are stated” so much as whether the expression is original and not somehow “donated” to the public domain by posting on Twitter. A serious argument can be made, with which I tend to agree, that Tweets inherently cannot be copyrighted, even IF original, because the very act of posting them on Twitter means the entire world can see them, without the author’s permission. So unlike other social media sites, where access to UGC can be controlled, at first blush it seems that unless one has a “private” Twitter feed, one cannot claim copyright in Tweets because the very nature of tweeting is that the tweeter intends that anyone in the world can view, link to and use his or her Twitter UGC.
(c) Tweets and Fair Use. Indeed, the underlying rationale for according Tweets copyright protection breaks down entirely when one examines fair use. First, if copyright applies to public Tweets, then traditional media’s use of them to date — including reading or displaying in full on television — cannot be fair use because it copies the entire “expression.” Second, the accepted practice of “retweeting” (RT) contradicts the basic principles of copyright law. Because users can (and do) retweet without limitation, it is a fair conclusion that posting a Tweet is an implied copyright license, at least for duplication by others on the same site. As Mashable’s Pete Cashmore noted, taking another user’s Tweets is not “copying,” but “retweeting. And I love it..” That comes at the question from the perspective of third-parties, rather than the putative content owner, but cogently expresses the idea that application of copyright to Tweets is problematic, at best.
Now it remains true that general legal rights and obligations can be varied by agreement. And to date, courts have largely accepted the de facto use of checkboxes to indicate a user’s “acceptance” of ToS contracts, drafted entirely by Web site owners, to which they have had no input or ability to negotiate. (California recently signaled a possible change to this assumption with a controversial decision as to software “shrink wrap” agreements, however.) So, assume we are now dealing with photos instead of 140-character messages. No one would argue that photos cannot be (or generally are not) copyrightable original expressions. So then — unless the act of posting itself is abandonment of a claim of copyright — ownership of rights on photos will be determined by the ToS of the social media Web site owner.
(d) Style or Substance? Here we have an interesting contrast. Facebook, as noted, has advocated a rather different view of copyright, insisting on a royalty free, perpetual license to UGC as a condition of posting — indeed, a license that survives death or withdrawal. Absent some independent constraint, like unconscionability, those ToS licenses are valid, regardless of a user’s rights under the Copyright Act. And Facebook has a point, because once “shared” with friends on the site, photos are (or at least can be) copied to some or all friends’ pages. Twitter, in contrast, says that UGC is always the user’s property. (As careful lawyers, however, Twitter’s counsel also include an express ToS license, even though retaining the “what’s yours is yours” language.)
This license is you authorizing us to make your Tweets available to the rest of the world and to let others do the same. But what’s yours is yours — you own your content.
Yet the inherently public nature of Tweets, which are “shared” with others by posting but not (except by retweeting) cross-posted as on Facebook, means that Twitter really does not need a license to the content of Tweets, since it does nothing with them other than what the user specifically intended, namely posting them on a Web page.
In the final analysis, this difference is probably more cosmetic than substantive, more about optics than legal rights. Twitter has designs to become the real-time Web’s “utility” infrastructure, so its business model does not require, indeed conflicts with, the company’s ownership or licensing of UGC. Facebook, in contrast, is a walled community, constantly devising ways for user to spend more time (whether or not productive or addictive) on the site. So for Facebook, and especially because any element of a Facebook profile can be made private, including to all other Facebook members, its buisness needs licensing for the model to work. They are different business models, driving different views of IP law. Just like beauty, in other words, the answer is in the eyes of those with the content itself!
And, BTW, if you think the above is thorny or complex, just ponder for a moment the even more opaque question of who owns UGC after the user dies. We’ve needed living wills and medical powers of attorney for more than a decade to exert personal control critical health care decisions. Will we also need Web-proxies authorizing our medical decision-makers and heirs to access and control UGC? Yup, you know the answer — “it depends.” A week or so after I first posted this essay, in fact, Facebook announced that it will “memorialize” profiles of deceased members if their friends or family request it. Facebook Keeps Profiles of the Dead [AP]. That may not be the law, as of now, but it does suggest that social networks will increasingly be required as a practical matter to develop their own policies, based on the interests and needs of their users, on how to address death in cyberspace.
In Part III of this series, we explore trademarks, genericide & “Twittersquatting.”
Last May I posted — in an article titled “Challenging DMCA Conventional Wisdom” — about a creative, but seemingly futile, effort by RealNetworks to plead its way around the Digital Millennium Copyright Act for yet another variant of DVD-ripping software. Well I missed the conclusion. In mid-August a federal court in San Jose (the Northern District of California) sided with the movie studios against Real, issuing a permanent injunction, and holding in a well-reasoned opinion in RealNetworks, Inc. v. DVD Copy Control Association, that Real had violated the DMCA.
So this is effectively the end of RealDVD. Calling the DMCA a series of “epochal amendments” to US copyright law, Judge Marilyn Hall Patel concluded that CSS technology “effectively controls access” despite having been hacked, finding that the statute is directed at preventing circumvention by the “average consumer,” and that Real’s CSS license was no protection because it had exceeded the scope of the license.
While it is true that no case has ever held that a licensee of the DVD [Copy Control Association] can be held liable for circumventing that same technology under the DMCA, that is simply because no court has ever adjudicated the issue. And, it may be that no licensee has been so bold as Real.
Perhaps the only amusing part of this rather sad escapade is the court’s observation that the RealDVD product was known internally as “Vegas,” because of the well-known marketing phrase “what happens in Vegas, stays in Vegas.” Secrets don’t hold up that well in Hollywood, on the other hand.
Yes, it is manifestly true that, led by the iPhone, of course, wireless Internet-enabled devices are chewing up bandwidth on 3G and other cellular networks at an unprecedented rate. But is that really a crisis? FCC Chairman Warns of “Looming Spectrum Crisis” for Wireless Devices.
I’ve got a lot of respect for Julius Genachowski. But on this point, I suggest he is all wet. Look at the historical parallels. Thomas Malthus warned more than 200 years ago of a food crisis as the industrial revolution expanded populations, and that did not happen either. In wireless data, the technology has advanced by an order of magnitude in just the past 3-4 years, like fiber optics using WDM to cram more capacity into the same amount of bandwidth. What is 3g today is almost 4G in Japan and other nations.
So don’t bet against technology. Increased efficiency in wireless data protocols — OFDM, for instance — trumps spectrum capacity all the time.
Posted via email from glenn’s posterous
There are lots of ways paternalistic regulation chafes against liberty and personal freedom, from helmet laws to consumer protection statutes. They personally drive me absolutely crazy. What business is it of government if as an individual one chooses to engage in “risky” behavior? Since I am paying (yes, a LOT of money) for my own health care, and have never once used as much in benefits as premiums, how do politicians get off forcing me to change my own activities to reduce what they cavalierly decide are socially-unacceptable activities?

It is one thing to give incentives to induce individual decisions beneficial to a country’s citizens as a whole, for instance tax credits for green appliances. But mandates are a completely different thing. What if I just adore incandescent bulbs and want to keep using them? What if, as is decidedly the case, I prefer to listen my iPod with ear-bud speakers and full volume, not using “soundcheck“? There is no conceivable reason I should not be permitted to do so.
That means, for me, that however much I like Europe — and as a Formula One fan it is certainly a very desirable continent — I would never live there. Just yesterday, the European Union parliament proposed requiring all MP3 manufacturers to put a volume “governor” on their products, to protect users’ hearing. EU to MP3 users: Turn that down!. Well, like Lynyrd Skynyrd, I say “turn it up!” This is paternalistic regulation at its worse.
Wait, you disagree? Sorry, couldn’t hear what you said.
Many are speculating that 2009 represents a fundamental turning point for the venture capital industry. Some are arguing that the industry is in dire straits after years of poor performance. Others have argued that the math simply does not work for the industry’s current size. What Is Really Happening to the Venture Capital Industry?
It is indeed quite likely that the venture industry is in the process of a very substantial reduction in size, perhaps the first in the history of the industry. However, the specific catalyst for this reduction is not directly related to the issues just mentioned. In order to fully understand what is happening, one must look upstream from the venture capitalists to the source of funds, for that is where the wheels of change are in motion.
The issue, explains Kevin Durant of abovethecrowd.com, is that a lack of liquidity and fairly ordinary returns from VC funds have driven institutional capital from the venture space. If so, it’s not that the IPO drought and absence of exit events for start-ups is what’s hammering Sand Hill Road, but rather a perfect storm of fiscal crisis and shrinking capital sources. That, coupled with the fact that VCs travel in packs and tend to jump on the bandwagon AFTER the innovation train has already left the station.
Yesterday the U.S. House of Representatives voted to restrict TSA from conducting what have become known as “virtual strip-searches.” House Restricts “Strip-Search Machines” [WashingtonWatch.com]. The bill provides, among other things, that:
Whole-body imaging technology may not be used as the sole or primary method of screening a passenger under this section. Whole-body imaging technology may not be used to screen a passenger under this section unless another method of screening, such as metal detection, demonstrates cause for preventing such passenger from boarding an aircraft.
Although promoted as less intrusive than x-rays, explosive sniffers and the like, this new technology presents a significant threat to personal privacy. As the sponsor (Rep. Jason Chaffetz, R-Utah) said, “Nobody needs to see my wife and kids naked to secure an airplane.” My colleague Chris Calabrese of the ACLU makes it graphically clear:
these machines produce strikingly graphic images of passengers’ bodies when they are utilized as part of the airport screening process. Those images reveal not just graphic images of “naughty parts,” but also intimate medical details like colostomy bags.
 "Privacy Screen" Filter Privacy advocacy groups are, for obvious reasons, alarmed. It is very much like the “Tunnel of Truth” hypothesized in the 1990 sci-fi film Total Recall. That was scary indeed! Not unsurprisingly, on May 31, a coalition of advocacy groups including the ACLU, the Electronic Privacy Information Center, Gun Owners of America, and the Consumer Federation of America sent a letter to Homeland Security Secretary Janet Napolitano asking her to “suspend the program until the privacy and security risks are fully evaluated.”
That will never happen. It its zeal to “protect” Americans traveling by air, TSA has turned the check-in experience into the U.S. equivalent of the Star Chamber, where ordinary citizens are presumed to be dangerous just by, for instance, wearing shoes — now routinely x-rayed separately at every U.S. airport — or putting liquids into carry-on luggage. The millimeter wave and related strip-search technologies ratchet this up yet another level. Use of a “privacy screen” to cover intimate areas is hardly an answer.
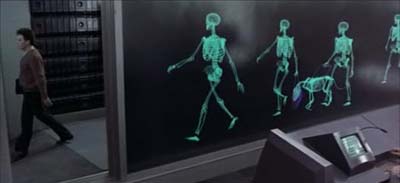
Tunnel of Truth (1990)
In my view, TSA is out of control. Yes, there were security lapses leading to 9/11, but they did not arise from business or vacation travelers and, with a bit more diligence (like following up on middle eastern males taking flying lessons but rejecting landing practice) the government could target those likeliest to have real terrorist connections. Just as TSA’s “no fly list” was overreaching, so is virtual body searching. We do not need this and we do not need TSA. I say abolish the agency, something with which Jim Harper of the Cato Institute, the premiere libertarian think tank, agrees.
|
|




